Quickstart
Let’s get started with ambient mesh. In this tutorial, you explore how to quickly set up an ambient mesh, add sample microservices, and enable secure mutual TLS (mTLS) communication between workloads.
Best of all, no changes are needed in your apps, because the mesh is ambient, or just there, working in the background. No config changes or app downtime to worry about.
Before you begin
Create or use an existing Kubernetes or OpenShift cluster.
Install ambient mesh
Our simple Getting Started script will install the Gateway API resources and the latest version of Istio, configured for ambient mode. Production installations are performed using Helm.
$ curl -sSL https://get.ambientmesh.io | bash -Congratulations! You successfully installed an ambient mesh!
Deploy a sample application
Let’s deploy the Bookinfo sample application to explore the security, observability, traffic control, and resiliency features in your ambient mesh. This app has four microservices that work together to create an online bookstore catalog. Separate microservices focus on sharing basic details about the book, user reviews, ratings, and the product page itself.
Deploy Bookinfo
Create the deployment and services for the Bookinfo microservices.
$ kubectl apply -f https://raw.githubusercontent.com/istio/istio/release-1.26/samples/bookinfo/platform/kube/bookinfo.yamlMake sure the Bookinfo pods are running.
$ kubectl get podsNAME READY STATUS RESTARTS AGE
details-v1-cf74bb974-nw94k 1/1 Running 0 42s
productpage-v1-87d54dd59-wl7qf 1/1 Running 0 42s
ratings-v1-7c4bbf97db-rwkw5 1/1 Running 0 42s
reviews-v1-5fd6d4f8f8-66j45 1/1 Running 0 42s
reviews-v2-6f9b55c5db-6ts96 1/1 Running 0 42s
reviews-v3-7d99fd7978-dm6mx 1/1 Running 0 42s
Create an ingress gateway
The Bookinfo pods are running, but how can you reach them?
Let’s create an ingress Gateway with the Kubernetes Gateway API. We’ll also create an HTTPRoute to set up routes to each of the Bookinfo microservices.
$ kubectl apply -f https://raw.githubusercontent.com/istio/istio/release-1.26/samples/bookinfo/gateway-api/bookinfo-gateway.yamlA brief note on the service types:
-
Using a cloud provider? You should be good to go. Istio creates a
LoadBalancerservice to expose the Gateway. Usually, your cloud provider assigns a public IP address or hostname for theLoadBalancerfor you. -
Don’t have or don’t want public access on a
LoadBalancerservice? You can annotate the Gateway to change the service type toClusterIP. This setup is common when you are testing locally, such as withkind.
$ kubectl annotate gateway bookinfo-gateway networking.istio.io/service-type=ClusterIP --namespace=defaultBefore moving on, let’s make sure the Gateway has an address and is Programmed:
$ kubectl get gatewayNAME CLASS ADDRESS PROGRAMMED AGE
bookinfo-gateway istio bookinfo-gateway-istio.default.svc.cluster.local True 42s
Access Bookinfo
Connect to the Bookinfo services through the Gateway that you just created.
Access the Gateway by port-forwarding its service.
$ kubectl port-forward svc/bookinfo-gateway-istio 8080:80In your web browser, open the productpage route: http://localhost:8080/productpage
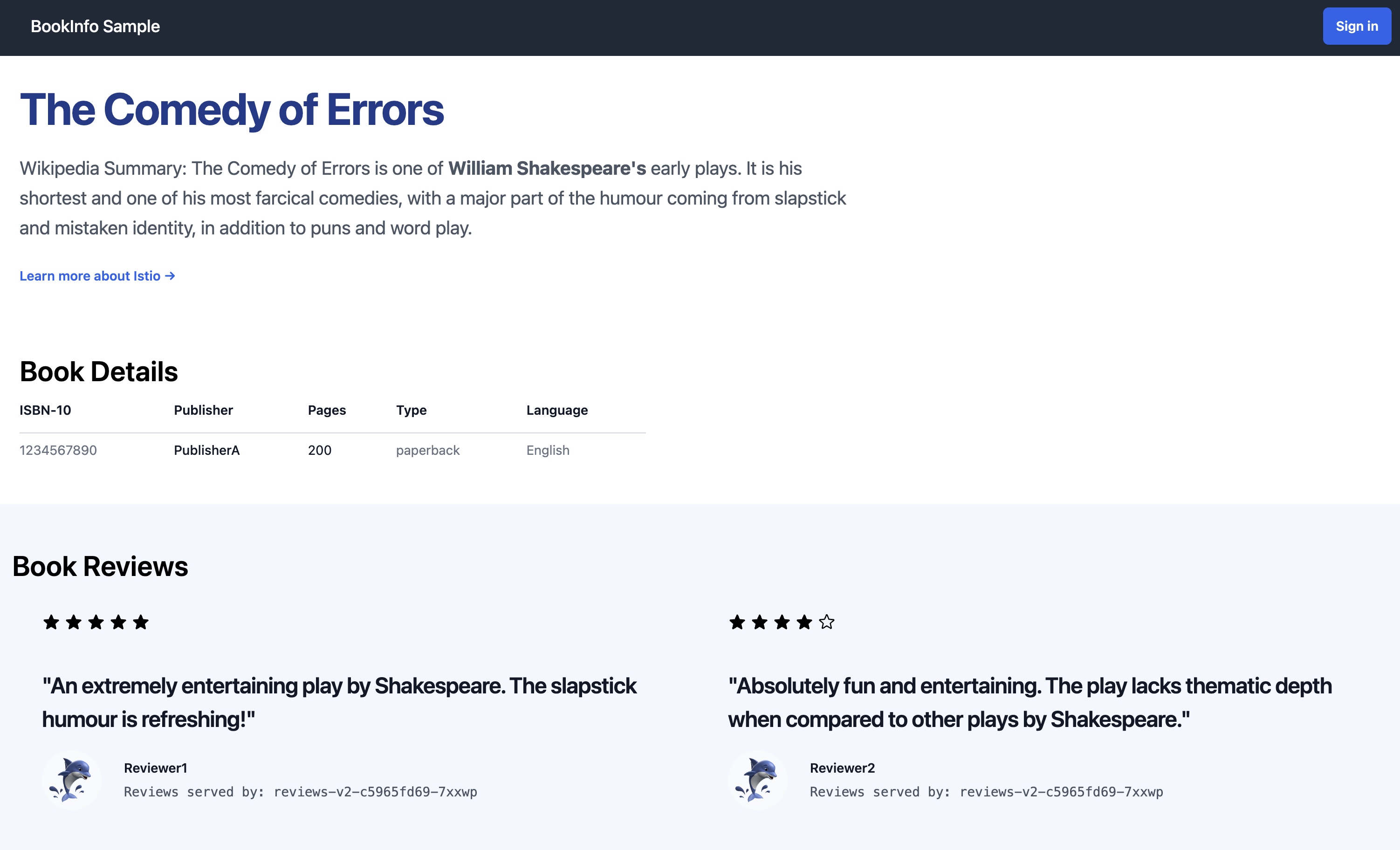
Refresh the page a couple times. You’ll see the book reviews and ratings change as the Gateway load balances your requests across the different versions of the reviews service.
To end the port-forward session in your terminal, enter Ctrl+C.
Nice job! Your Bookinfo app is up and running.
Add Bookinfo to the mesh
Adding applications to an ambient mesh is as simple as labeling the namespace where the application resides. By adding the applications to the mesh, you automatically secure the communication between them via mutual TLS (mTLS). No restart or redeployment of your applications are needed. As traffic is routed through your ambient mesh, TCP telemetry data is automatically collected for you.
$ kubectl label namespace default istio.io/dataplane-mode=ambientnamespace/default labeled
That’s it! You successfully added all pods in the default namespace to the ambient mesh. 🎉
What does that mean?
When apps join the mesh, ambient mode automatically secures the communication between them via mutual TLS (mTLS). It also automatically collects TCP telemetry data for you. And no, you don’t need to update any config or redeploy your apps!
If you open the Bookinfo application in your browser, you see the product page, just like before. But this time, the communication between the Bookinfo application pods is encrypted by using mTLS.
Verify mTLS using observability tools
Kiali is an observability console for Istio, and you can use it to verify that your traffic is indeed encrypted.
Install the monitoring tools
Kiali depends on Prometheus, which is used to collect and aggregate metrics from the Istio components. To install sample installations of both:
$ kubectl apply -f https://get.ambientmesh.io/monitoring.yamlAccess Kiali by port-forwarding its service
By default, Kiali is only accessible from inside the cluster. Like the Gateway above, we can access this service by port-forwarding.
$ kubectl port-forward svc/kiali 20001:20001 -n istio-systemYou can now access Kiali on localhost port 20001.
Open Kiali to the traffic graph page
In another browser, open Kiali to the traffic graph page. Using that link, you also automatically enable the feature to display security badges.

The padlock icons on all the graph edges, indicating the traffic is encrypted with mTLS. (If you don’t see them, click “Display” at the top and scroll down to “Security badges”.
Clicking on an edge between two services will show you the identities that are being used. In this example, you can see that they relate to the service accounts for the ratings and reviews services in the default namespace.
Next steps
Just by setting up ambient mesh, you’ve already unlocked many benefits like automatic mTLS across apps. Now, explore all the other things you can do with ambient mesh.